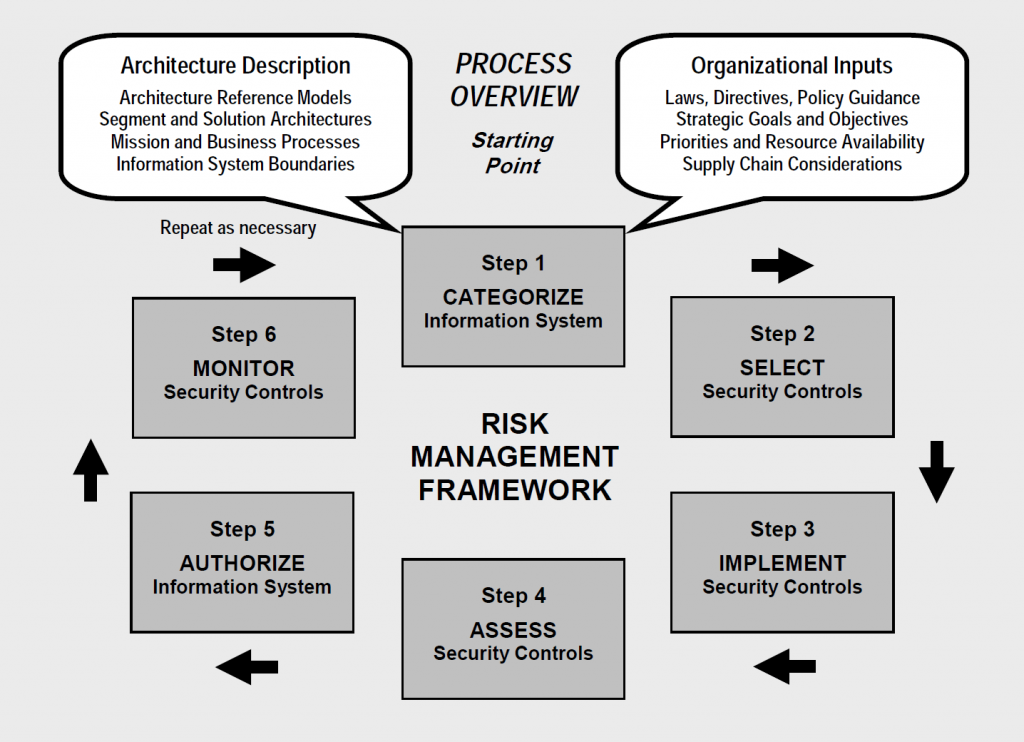
Companies started the year executing their normal slate of plans and projects, but in March everything came to a screeching halt because of the COVID-19 pandemic. Since then, many have been so busy keeping the lights on that most, if not all, non-essential activities have been put on the back burner, if not shelved altogether.
Regulatory compliance activities have also taken a backseat and will perhaps continue to do so unless things rapidly normalize. While a lot of assistance and extensions are being afforded to businesses and households alike for mortgages and other monthly payments and even tax return filings, it is highly unlikely there will be any exceptions or exemptions made to regulatory obligations and due dates. Complying with the Payment Card Industry Data Security Standard (PCI DSS), Health Insurance Portability and Accountability Act (HIPAA), Federal Information Security Management Act (FISMA), New York Department of Financial Services (NYDFS) Cyber Security Regulation, Federal Financial Institutions Examination Council (FFIEC) standards, and more will still apply per usual.
If anything, these standards designed to thwart cybercrime will only tighten as security risks have grown exponentially due to the huge surge in telecommuting. While many organizations successfully enabled large numbers of employees to work at home, they also became more vulnerable to security issues. Poorly protected devices, alongside personal devices with no known protection used by employees not trained in digital security, represented a serious risk. That combined with the sharing and displaying of financial, sales, and other confidential information via poorly protected web conferencing and collaboration tools has resulted in extraordinary exposure of confidential data. The consequences of which are more than likely to appear on the horizon.
Companies will somehow get to the traditional data security compliance obligations mentioned previously but may miss the newer SWIFT Customer Security Programme (CSP) mandate. In force since 2017, SWIFT CSP is really ramping up this year, adding new Customer Security Controls Framework (CSCF) v2020 requirements. And with good reason—SWIFT moves a huge portion of the world’s money and a single weak link in the financial messaging network can wreak havoc on the entire community. Fortunately, SWIFT CSP is one of the better security standards around. It is very well defined, easy to understand and act on, and has requirements that are not onerous.
SWIFT Users Should Prepare Now
Every SWIFT user must complete a Know Your Customer (KYC) Security Attestation application and submit their organization’s self-assessment data before December 31, 2020. The assessment confirms an organization’s level of compliance with SWIFT’s customer security controls and must be conducted by an external third-party or an internal independent function. SWIFT makes self-assessment results available to all SWIFT users for total network-wide customer visibility. It is a very fair and transparent system that benefits all stakeholders.
So, what does this mean for organizations? A lot if an organization is engaged in international remittances.
If another SWIFT member, bank, or corporate entity wants to send money to credit a customer account, they are at liberty to look up the receiver’s security posture on the SWIFT website. If they are not comfortable with the organization’s level of compliance, they can refuse to conduct SWIFT transactions with them. Similarly, organizations transferring money to another SWIFT customer can refuse to accept and credit transfers to the recipient account specified, leaving the originator in limbo.
Initially, SWIFT takes an easy-to-follow approach with CSP. However, if a customer’s security self-assessment is found to be sketchy or unreliable upon examination, or if other customers have been reluctant to transact with an organization, SWIFT will insist the customer undergo a full-blown third-party infrastructure audit. After audit completion, network access can be temporarily or permanently shut down as organizations work to remedy identified deficiencies.
This is harsh, but the outcome of complying with SWIFT CSP is far more positive. It provides easy and clear guidance to make sure SWIFT infrastructure is secure and ready so that customers can continue providing high-quality transactional services to customers and protect their reputations.
The Bottom Line: Despite the current pandemic environment, companies are well-advised to start working on SWIFT CSP compliance in the second half of 2020 to make sure they can continue to fully serve customers without putting their reputations and businesses at risk.