The Second Pillar of Information Security: Risk Management Lifecycle
Posted by Buck Kulkarni on 08 May 2018


In my last blog, I introduced readers to the two pillars of Alacriti’s information security program:
- Strong information security policies
- A comprehensive risk management lifecycle
There I detailed the information security policies that comprise our current approach, including how they’ve helped us present a sustainable security and compliance posture to scores of annual certification audits and client assessments. I also wrote briefly about the importance of a comprehensive risk management lifecycle, which is the second pillar of our program. I’ll now go into more detail about the risk management lifecycle and how we approach it here at Alacriti.
Security policies, procedures, logging and monitoring systems, incident handling, and internal audits are all necessary tools to achieve and sustain a strong security posture. However, they also pose a risk for organizations. These tools allow us to go deep into the target domain (for example firewall controls, encryption, or incident management) to achieve a strong capability. However, they can also blind us to the breadth of the canvas. Or to put it another way, we can run the risk of missing the forest for the trees.
A good risk management framework (RMF) helps create a complete picture of an organization’s risk canvas so we know that we’re expanding the breadth of our view at the proper rate. Of course, there will never be resources (the good old troika of time, expertise, and money) to do it all. Therefore, priorities must be made according to risk levels, regulatory priorities, and current audit issues. The beauty of the RMF is that it will remind organizations of the major gaps in their defenses that require attention. This can help prevent organizations from thickening the fort walls in one area while leaving others unintentionally exposed.
Alacriti adopted the NIST body of knowledge as the foundation for our risk management program. Over the past decade, we built our risk management program upon a foundation that’s comprised of RMF, policies and procedures, controls (by family), and evidence gathering and management.
This body of knowledge also comes with a huge set of topical guidance that we use to develop topic-specific policies and procedures. A special publication called the NIST SP 800-37 is the foundation of the RMF. Several American information security regulations are either based on this or draw on its framework including FISMA, HIPAA, FedRAMP, FIPS, DoD, and others. This has given us the advantage of being able to comply with multiple regulations from the same baseline effort.
A quote from The Office of the Chairman of the National Strategy for Cyberspace Operations (DoD) made in relation this standard is a useful point of reference for decision makers from all sectors. It says, “For operational plans development, the combination of threats, vulnerabilities, and impacts must be evaluated in order to identify important trends and decide where effort should be applied to eliminate or reduce threat capabilities; eliminate or reduce vulnerabilities; and assess, coordinate, and deconflict all cyberspace operations.” It helps us focus on the entire canvas from threats to impacts, trends to experiences, and eliminating to resolving. That is the heart of risk management.
The NIST SP 800-37 presents the following risk management lifecycle for practitioners:
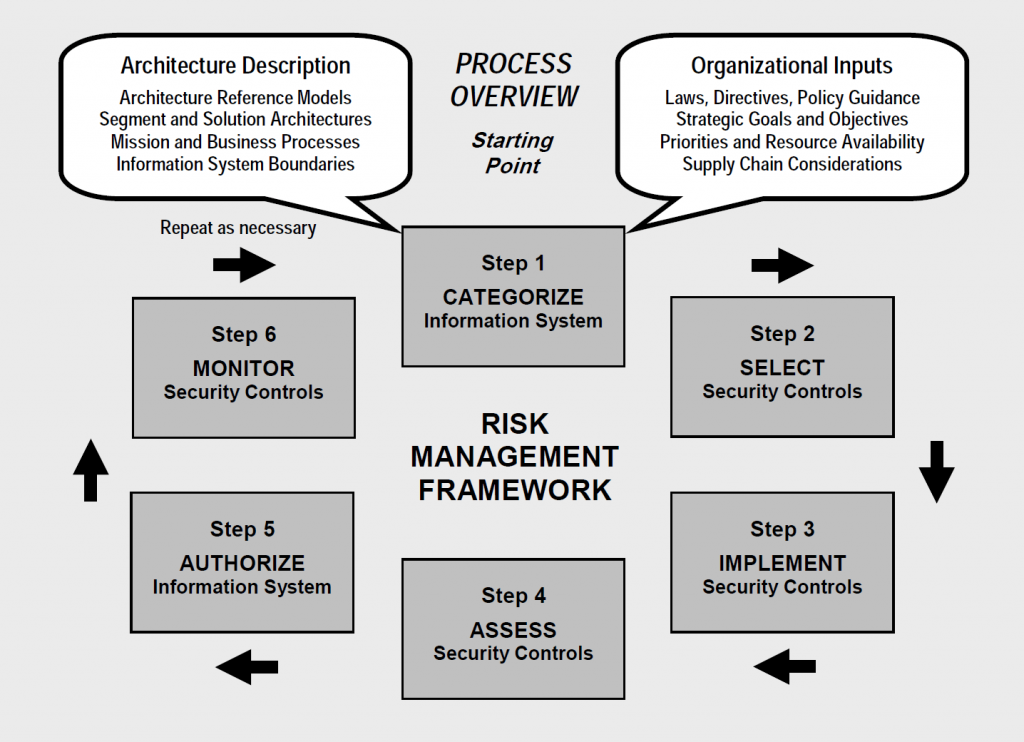
The cycle does not need any explanation however I will share a few lessons that we’ve learned along the way. First for foremost, make sure your technology and legal/compliance functions come together to define this and prevent it from being “thrown over the wall” amongst groups. Secondly, make sure they don’t try to win the day with jargon because both sides have plenty of it. Thirdly, don’t try to boil the ocean – you can never have a large enough fire to do that. Start by addressing low-hanging fruit like immediate audit items but be sure to use the RMF so no one loses sight of the full picture. Finally, make sure to keep this process iterative. It is a program, not a project.
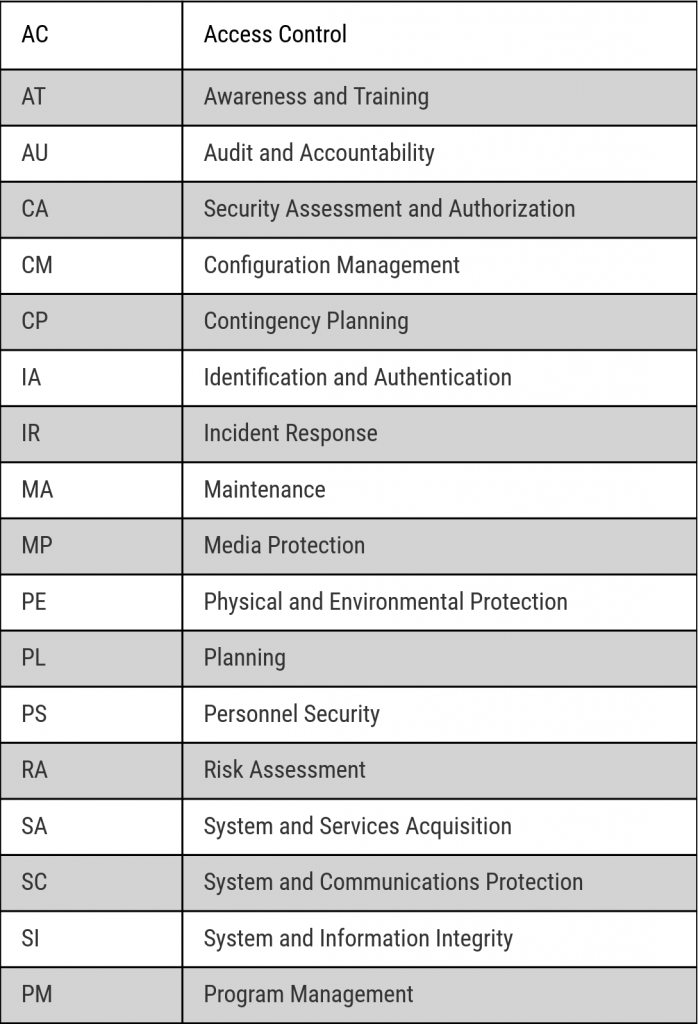
When you mesh the control families that the NIST defines (see SP 800-53), a cohesive picture will begin to emerge that empowers you to make progress with decreasing effort over time. Most importantly, the experience of our compliance efforts waxing and waning (as many of the efforts are risk or topic driven) has changed to a sustainable posture over time. This has created a solid foundation in the face of changing regulations, infrastructure, applications, and over events outside of our control.
Here is a quick overview of the NIST Control Families. You can designate different teams to focus on specific families and use the risk management lifecycle approach to achieve continuous improvement in their respective areas. This allows the team to adjust their speed based on other pressures while also ensuring that nothing falls through the cracks.
The Bottom Line: At Alacriti, we live with 24x7x365 real-life risks. Our infrastructure and applications are under constant threat from entities that mean us harm. In addition, we must comply with ever-expanding regulations that apply to our clients in the financial services, healthcare, payment processing, and government realms. Our experience shows that adopting a comprehensive, flexible risk management framework provides a powerful toolkit to your technology, security, and compliance professionals.
Please Note: All quotes, references, and diagrams related to NIST are from NIST's official documents and websites.
Schedule A Personalized Demo
Schedule a Free Consultation





